Vulenversity -Writeups
step by step execution
Prerequisites:
Nmap
Directory Busting(Gobuster)
Burpsuit
Linux file systems, Permissions, SETUIDs, environmental variables, etc
Objectives:
- Gather Information about the target machine
- Find out hidden directories on the webserver
- Gain Shell of the webserver
- Escalate privileges.
Getting Started
[Task 1 ]- Deploy The Machine
First, we need to connect to the TryHackMe network using OpenVPN. The procedure is pretty straight forward you just need to download the configuration and run it using the OpenVPN command on the terminal. Once done verify that you are on the network of TryHackMe by using the ifconfig command on the terminal, you should see an interface named ‘tun0’ or ‘tun1’ and an IP assigned to it. Congratulations you have now connected to the TryHackMe network.
[Task 2 ]- Reconnaissance
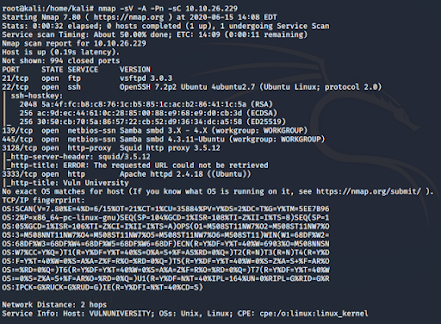
First, we need to gather information regarding the target machine by scanning it using Nmap as shown below. There are certain switches while using Nmap which will fetch information accordingly such as -A switch performs an aggressive scan. You can find more information on what others switches do by consulting the manual for Nmap.
Nmap Scan for the target machine
From the above scan, we get the number of open ports. In addition to this, we also find the services and versions of services running on each of the open ports. Using the -o flag Nmap gives us the operating system of the target machine as shown below. If we use -n flag it will not resolve the DNS (IP to Host-name)
[Task 3 ]- Locating directories using Gobuster
Now that we have the information about the ports and services running on them. Let’s try to explore the HTTP service running on port 3333. The following page opens when we access it by using the IP of the target machine and port 3333. Exploring it does not give much of information.
The output result shows the available hidden directories out of which most of the directories are normal and found on most webpages. /internal looks interesting so when accessed it showed a page that had an upload option. So are you thinking what I am thinking? If you guessed it right things are going to get pretty interesting from here.
Upload Restriction
I used wapalyzer and found out that the website is built on PHP so it’s quite understandable that .php is not allowed because if the same extension is allowed that of the site an adversary may make the file executable and gain shell access to the webserver.
Now to know which extension is allowed on the web server so that we may get a shell, fire up Burp Suite. Remember to configure the proxy on the web browser so that the traffic may get intercepted by Burp Suite via this proxy.
Set the attack target as shown below:
Set Attack Target and Port
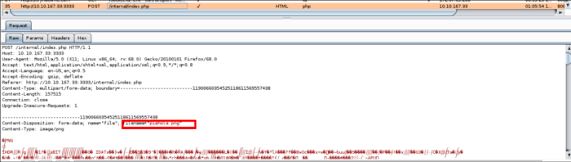
Now upload any extension file on the upload page of the webserver so that the request gets captured in HTTP history as shown below. Don’t forget to turn on the interceptor.
Send this request to the intruder and mark the field of extension. We are going to fuzz that field to find out which extension gets bypassed easily.
Intruder
In the payload option, we are going to upload the extensions that would be fuzzed. Don’t forget to uncheck the encode option as keeping it enabled will not give you the correct results.
Selection of payload for fuzzing
Now navigate to the options add the grep match i.e. the output message that displays when a wrong extension file get uploaded.
Now click attack and this will begin the fuzzing process. As seen below we see that the .phtml extension is allowed on the webserver. We can confirm this in two ways, one is the length and the other is the response of the webpage against this extension in the raw tab.
Fuzzing Started
Now that we know that .phtml extension is allowed. Its time to upload the PHP shell. The PHP shell to be uploaded can be found here. Edit the script by adding the local IP address of your machine that can be found by typing the ipconfig command in the terminal. The IP against tun0 or tun1 has to be copied and added into the script. Before uploading the script let us use Net-cat to listen to incoming connections on port 1234 as shown below.
netcat listening on port 1234
Upload the PHP script on the internal webpage of the server, we will see that the script has been uploaded successfully.
` Uploaded .phtml script
Navigate to http://<ip>:3333/internal/uploads/php-reverse-shell.phtml.As soon as we navigate to this URL we will get a reverse shell as shown below.
Reverse Shell Access
Now we need to find the user that manages the server. Navigating to the etc/passwd file we get to know that there is only one user that has bash access so based on this assumption we come to know about the as shown below.
etc/passwd file
Navigating to the user directory we get the user flag.
[Task 5] Privilege Escalation
Now that we have the shell access, we need to escalate our privileges to root. This section is quite tricky and expects that you know about the setuid function and Linux permission stuff. A little theory is already explained regarding this function. If we see the current permission on our user we don’t have root privileges.
Let list out all suid files by using the following command.
find / -user root -perm -4000 -exec ls -ldb {} \;
systemctl stands out of all other files which have setuid enabled because it’s not normal to have setuid enabled on systemctl. I got curious and ran the same command on different hosts and found that none of them had the systemctl with setuid enabled so based on this /bin/systemctl stands out. gtfobin is a great place where gtfobin is a great place where you can find Unix binaries that help in privilege escalation bypassing the local security policies.
Now we need to set up an environmental variable. I have changed the above script a bit like I would prefer to get the bash of the privileged user so I have edited it as seen below. To get all the things right, you might want to get an overview of the Linux file system and setuid.
After this step enable the environmental variable created and run it. As soon as we execute this we get the root privilege and our root flag too as seen below. The euid and egid are root now.
With the last task performed successfully we conclude this walk-through. I know the last part has been overwhelming but don’t worry I would be writing on Linux privilege escalation soon that would clear all your doubts. Now we know how we can bypass upload restrictions on the webserver and exploit it to get a shell of the webserver.....



















hii
ReplyDelete